The following is summary of three insightful blog posts by Natto Team, an emerging threat intelligence team focused on the human, language and geopolitical aspects of cyber threat intelligence. I encourage readers to read the primary sources when they have time due to amazing details on Chinese scanning capabilities.
We have summarised this reporting as scanning is the key first step of cyber reconnaissance activities. The Internet 2.0’s Cloaking capability does mitigate all open information provided by scanning tools when we conducted initial analsyis of these insights.
Decoding the i-SOON Leaks
The initial Natto Team's analysis of leaked documents from the Chinese hacker-for-hire company i-SOON reveals the prominence of "TZ," an enigmatic acronym appearing frequently in various documents. Despite extensive mentions, its precise meaning remains elusive. Natto Team speculates that "TZ" might denote "special investigation" or "special reconnaissance," indicating a focus on network security and cyber capabilities. This aligns with the Chinese Public Security Bureau’s emphasis on building specialized network teams for cybersecurity tasks, emphasizing the importance of reconnaissance in cyber operations.
APT41's Reconnaissance Techniques
APT41, a company with affiliation to i-Soon and a Chinese attributed state-sponsored hacking group, also leverages sophisticated reconnaissance techniques to gather critical information about targets. Their toolkit includes both globally recognized tools like Nmap and specialized Chinese-developed tools such as OneForAll and Subdomain3. Techniques like Execution Guardrails enable APT41 to limit malware activation to specific targets, enhancing stealth and reducing detection risk.
Comprehensive Review of Scanning Tools
To understand the scope and capabilities of the tools used by Chinese cybersecurity firms and state-sponsored groups like APT41, Natto Team took a deep dive into the tools.
1. Nmap (Network Mapper)
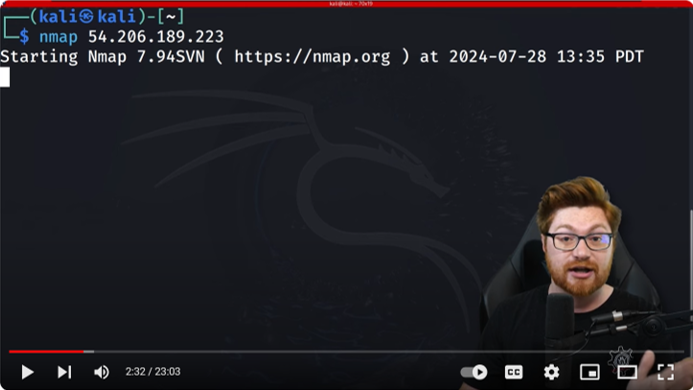
Nmap is a free and open-source network scanner used for network discovery and security auditing. In China, Nmap has been widely adopted not only by cybersecurity firms but also by hacking groups due to its robust feature set and versatility. It can:
- Identify active devices on a network.
- Discover open ports and services.
- Detect operating systems and hardware addresses.
- Perform version detection and scriptable interaction with the target.
Nmap's popularity is evident from its widespread availability on Chinese websites, tutorials, and even training videos from platforms like 51CTO, which caters to millions of IT professionals.
2. OneForAll
OneForAll, developed by Chinese coder Jing Ling, is a powerful tool for subdomain enumeration. This tool is particularly noted for its ability to pull data from unique Chinese data sources like Baidu Cloud Observation and Gitee, which are typically not accessed by non-Chinese tools. Features include:
- Subdomain blasting and verification.
- Subdomain takeover detection.
- Integration with various data sources for comprehensive subdomain discovery.
OneForAll’s ability to leverage local Chinese data sources gives it a distinct edge in regional cyber operations.
3. Subdomain3
Subdomain3 is another tool designed for subdomain discovery. Developed by a Chinese coder under the GitHub handle "yanxiu0614," Subdomain3 is recognized for its efficiency and effectiveness in:
- Bruteforcing subdomains using predefined wordlists.
- Integrating with other reconnaissance tools for extended capabilities.
- Providing a user-friendly interface for rapid deployment and scanning.
Its development by a local coder and tailored features make it a go-to tool for both defensive and offensive operations in China.
4. SubDomainsBrute
SubDomainsBrute, hosted on GitHub by "lijiejie," is specialized in subdomain brute forcing. It uses common subdomain names to attempt connections, aiding in uncovering hidden assets of a target organization. This tool's key aspects include:
- Comprehensive wordlists for extensive subdomain coverage.
- High-speed brute forcing capabilities.
- Integration with other tools for combined reconnaissance efforts.
5. FOFA
FOFA is an internet asset search engine developed by Beijing Huashun Xin’an Technology Co. Ltd. It is comparable to Shodan and Censys, focusing on:
- Identifying connected devices and services worldwide.
- Leveraging a vast database of over 4 billion internet assets.
- Offering advanced search functionalities to filter results based on specific criteria.
APT41 uses FOFA extensively for passive reconnaissance, making it a critical component of their operational toolkit.
Other Popular Chinese Scanning Tools
In addition to the aforementioned tools, several other Chinese-developed scanning tools are worth noting due to their capabilities and prevalence in the cybersecurity landscape.
6. X-scan
X-scan, developed by the hacker group Xfocus, is a comprehensive network vulnerability scanner known for:
- Command-line and GUI front-end operation.
- Identifying a wide range of vulnerabilities across different network services.
- Integration with other security tools for enhanced scanning and reporting.
Xfocus's historical significance and continuous development of X-scan underscore its importance in China's cybersecurity toolkit.
7. ZoomEye
ZoomEye, developed by Knownsec, is a powerful search engine for internet-connected devices and services. It is known for:
- Identifying industrial control systems (ICS) and other critical infrastructure components.
- Providing detailed information on devices, including IP addresses, operating systems, and open ports.
- Offering advanced search capabilities to uncover potential vulnerabilities.
ZoomEye’s focus on ICS makes it particularly valuable for targeting critical infrastructure.
Key Insights
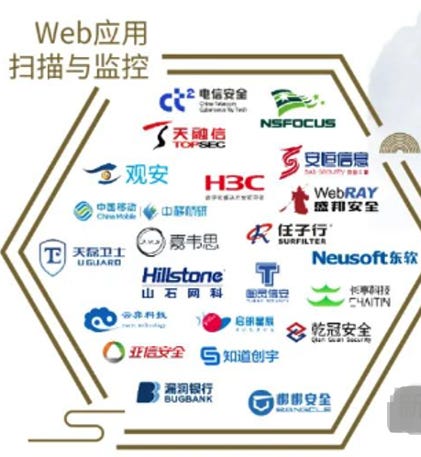
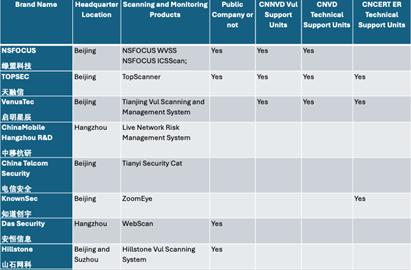
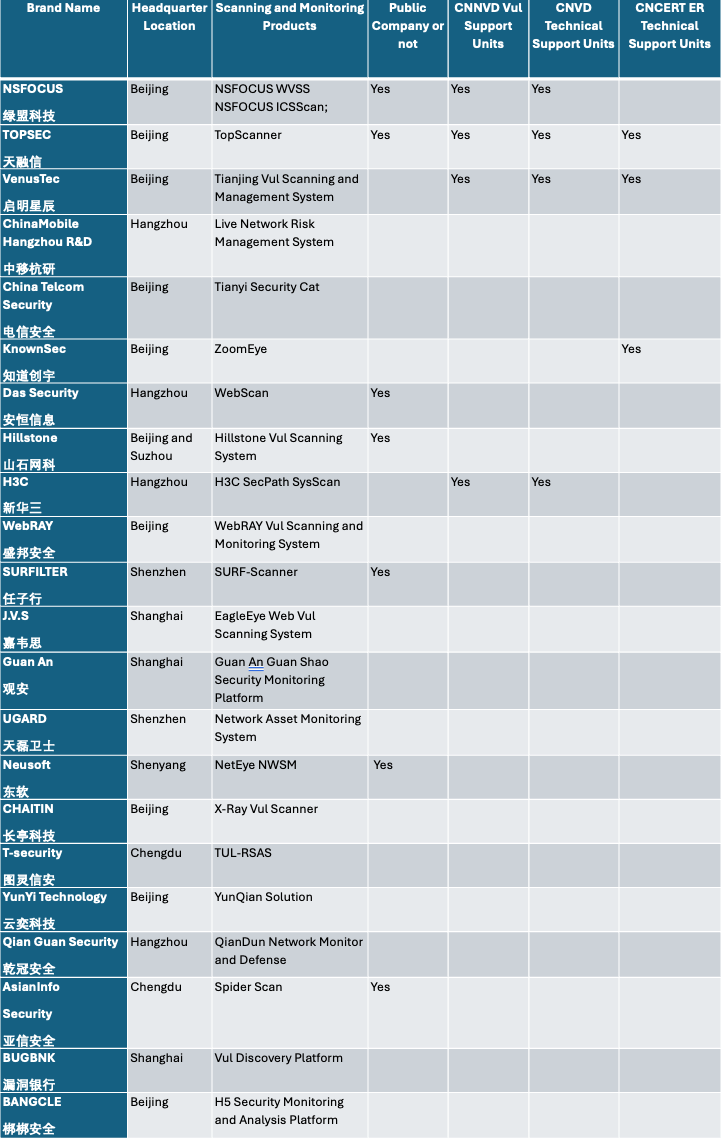
Natto Team has been auditing many cyber security companies. The below table is their analysis of which company is using which tools.
Conclusion
The comprehensive analysis of i-SOON's leaks, APT41's techniques, and the broader cybersecurity industry highlights China's sophisticated and multifaceted approach to cybersecurity reconnaissance. The Natto Team’s insights offer a valuable perspective on the intricate dynamics of this capability, emphasizing the critical role of reconnaissance China’s cyber security industry.
Original Natto Blogs: