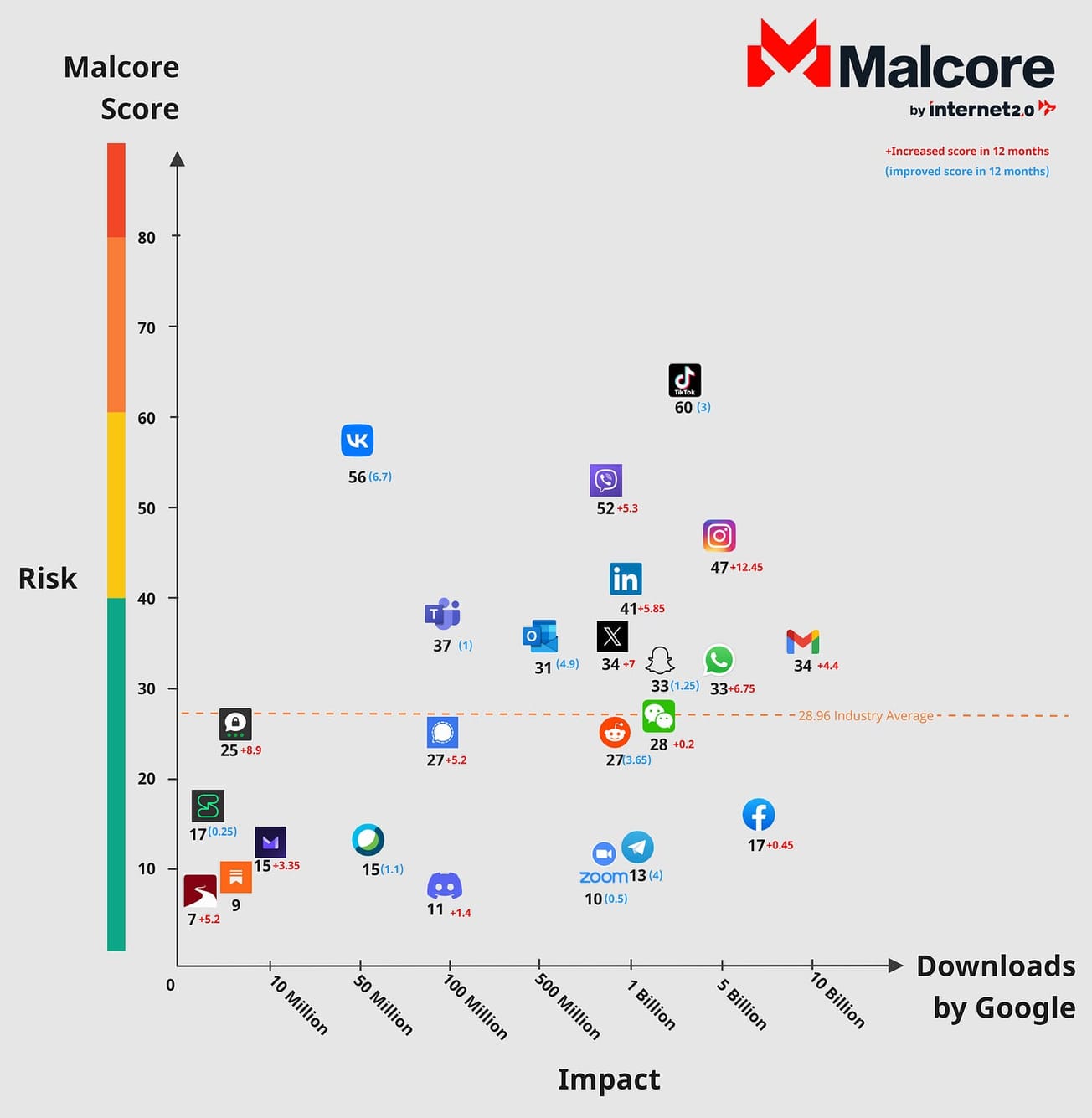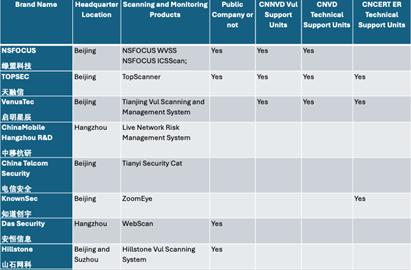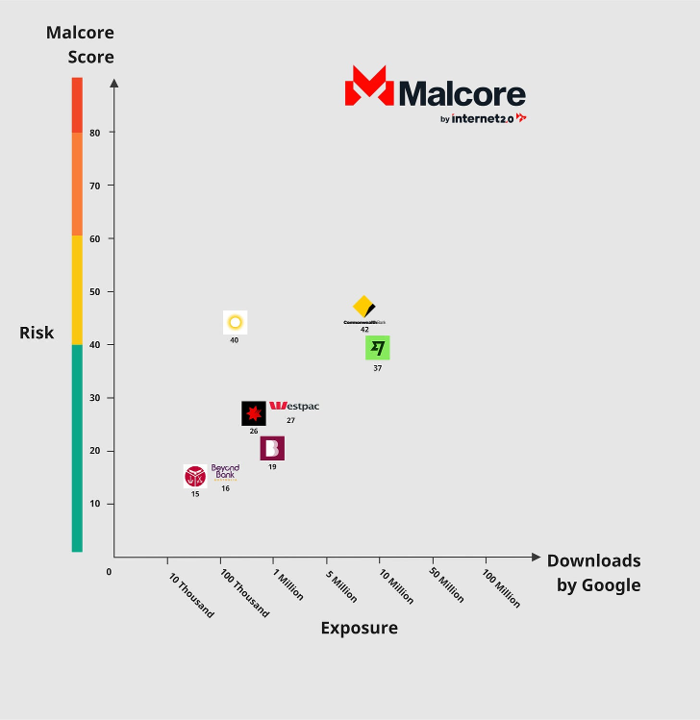
Featured
Contec CMS8000 Patient Monitor
Abstract: The Contec CMS8000 Patient Monitor is a medical device designed to provide real-time monitoring of vital signs. This report provides a comprehensive analysis of the device, revealing critical security vulnerabilities that pose a risk to patient privacy, data integrity, and overall system security. This analysis examines the device'