On February 19, 2024, a leaker posted a meticulously curated trove of documents on GitHub from Sichuan Anxun Information Technology Co., Ltd. (四川安洵信息技术有限公司), the company behind the website i-soon[dot]net. The authenticity of these leaked documents has been verified by the Associated Press, who anonymously interviewed two employees confirming, "i-SOON and Chinese police are investigating how the files were leaked."
This leak represents a significant revelation, indicating China's implicit involvement in the extensive cyber warfare conducted by its private enterprises on a global scale. The Chinese government's support is evident through contractual relationships, protective measures, and public expressions of support.
Why does it matter?
Based on the available trove of documents, I assess with high confidence that i-SOON possesses both the capability and intent to conduct hacking operations on a large scale against foreign governments and their critical infrastructure. For many years, they have openly referred to their hacking activities as APT (Advanced Persistent Threat) activities, demonstrating a brazen attitude towards their actions.
A list of countries where there is evidence suggesting i-SOON had the intent to hack or had already compromised organizations includes:
Afghanistan, Australia, Bosnia and Herzegovina, Britain, Cambodia, Congo, Djibouti, East Timor, Egypt, Ethiopia, France, Guinea, India, Indonesia, Kazakhstan, Kyrgyzstan, Malaysia, Mongolia, Myanmar, NATO, Nauru, Nepal, North Macedonia, Oman, Pakistan, Palestine, Peru, Philippines, PNG, Romania, Rwanda, South Africa, South Korea, Taiwan, Thailand, Turkey, the United States of America, and Vietnam. For a comprehensive overview of this evidence, please click here.
Based on the document trove available I assess with high confidence that i-SOON has the capability and intent, and had already for many years been conducting, hacking operations at scale against foreign countries governments and their critical infrastructure. They have referred to their hacking activities as APT activities and shown a brazen openness to the facts of their hacking.
A list of countries that there is evidence they had the intent to hack or had already hacked organizations within these jurisdictions are Afghanistan, Australia, Bosnia and Herzegovina, Britain, Cambodia, Congo, Djibouti, East Timor, Egypt, Ethiopia, France, Guinea, India, Indonesia, Kazakhstan, Kyrgyzstan, Malaysia, Mongolia, Myanmar, NATO, Nauru, Nepal, North Macedonia Oman, Pakistan, Palestine, Peru, Philippines, PNG, Romania, Rwanda, South Africa, South Korea, Taiwan, Thailand, Turkey, United States of America and Vietnam. For a complete accounting of this evidence see here:
i-SOON is closely affiliated with the Chinese government as a supplier of software and cybersecurity services. They engage regularly with government officials in their capacity as a business entity and have obtained a secret military clearance to supply the defense industry. Additionally, they have touted their work in support of Chinese government security services as a mark of credibility for their company.
Financially and contractually, i-SOON is linked with the notorious hacking group APT41, which is a top-priority target for the US Department of Justice, having already been indicted. The US government alleges that APT41 has been involved in various criminal activities, including the theft of tens of millions of dollars in US COVID relief benefits since 2020, as well as the theft of counterfeit goods, pirated software, and trade secrets, amounting to an annual loss of up to $600 billion for the US.
What's the impact?
Governments worldwide, including those of India, Thailand, and Nepal, will likely demand justice and answers in response to these revelations. APT41's status as a major target for the US government, coupled with their financial ties to i-SOON, may lead to i-SOON being placed on the sanctions target list.
Given i-SOON's strong relationship with the Chinese government, it remains uncertain whether China will shield i-SOON from international repercussions.
The diplomatic tensions arising from this situation are likely to agitate the Chinese Ministry of Foreign Affairs, prompting inquiries into the cause of the leak.
Why are we cautious of this leak?
This leak appears to be meticulously curated, potentially orchestrated by parties seeking to damage i-SOON's reputation and provoke action from Chinese authorities and governments worldwide. Fully verifying the authenticity of this leak is challenging unless the victims come forward to confirm each piece of evidence. The data has been noticeably cleansed and structured to inflict maximum reputational harm on i-SOON, with specific details about prices and APT41 being deliberately omitted or redacted at key points.
Who is Shutdown?
吴海波 Wu Haibo aka "shutdown" registered the original company website i-soon[dot]net to the email [email protected]. An article online in China basically names him as a member of the 绿色兵团 Green Corps. Wu Haibo is the CEO and ultimate beneficiary of i-SOON. The article describes the Green Corps as a pioneer hacking group in China founded in 1997 and was also called the "Whampoa Military Academy" by the hacking community.

APT41 links deep dive:
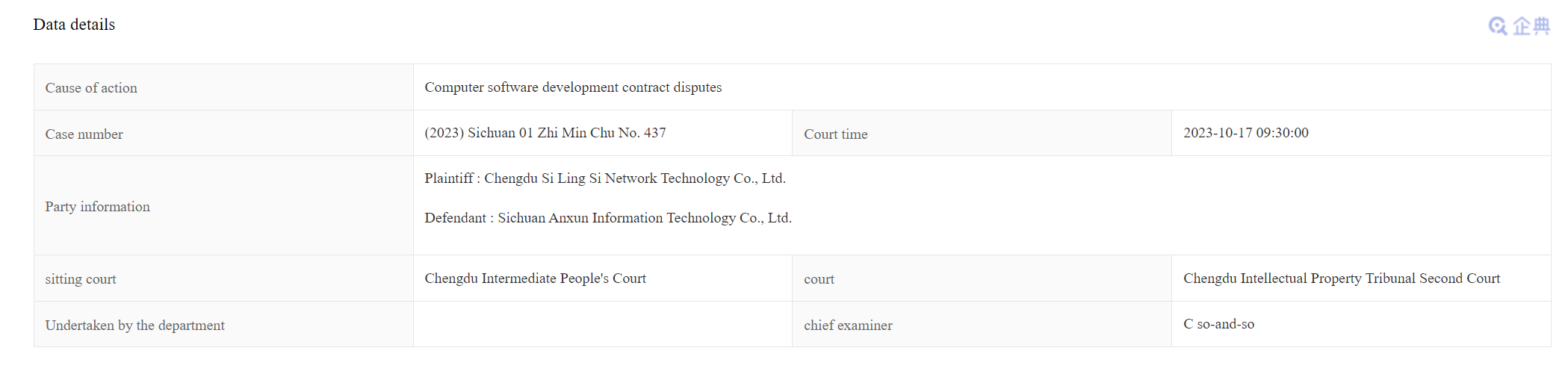
i-SOON, has been to court in 2023 with a Chengdu Si Lingsi (404) Network Technology Company Ltd. (成都市肆零肆网络科技有限公司). Established in 2014, it is better known colloquially as Chengdu 404 or APT41. This dispute is over a computer software development contract suggesting they have had a financial relationship with APT41.
Chatlogs between 吴海波 Wu Haibo aka "shutdown" the CEO and owner of i-SOON and his second in command 手陈诚 Chen Cheng aka "lengmo" on APT41
2020-09-16 23:51:18
lengmo: FBI adds 5 Chinese APT41 hackers to its Cyber's Most Wanted List. Fuck. Hold. problem occurs. 404 exploded.
Shutd0wn: Awesome
lengmo: my day. There are photos
Shutd0wn: Ha ha ha ha. No. 41. Next time I drink, ask them to drink 41 drinks.
Shutd0wn:(Chatlog has been erased)
Shutd0wn: What valuation statement do they have?
lengmo: It can be said later that they are all certified by the FBI. I saw roses in there too. It doesn’t take long to explain There are 5 in total, and there are 4 in our group. [Awkward][Awkward]
Shutd0wn: 404 is already tied to Aerospace Science and Industry, right?
lengmo: Um
Shutd0wn: We have no key to cooperation with 404, right? association.
lengmo: No. Does accompanying the bid count?
Shutd0wn: They are all members of the Drinking Council. On the 14th, two accomplices were arrested in Malay.
Shutd0wn: [Panic]
2020-09-17 00:19:302020-09-24 04:30:15
lengmo: 😂😂A guy from 404 who does security development and research submitted his resume. Awkward. Recruit or not
Shutd0wn: trick
lengmo: Are there any risks involved in researching that? Asking me
Shutd0wn: What does this person do? If it doesn’t involve business, it doesn’t matter.
lengmo: Technical. Development of some tools and 🐎 etc. Still a girl. fresh graduate. She looks pretty good, Ji Yunhui is very excited
Shutd0wn: Ha ha. Do you have a photo
lengmo: HR and I emphasized that 404 people are mainly not recruited by us on our own initiative. This is not possible and cannot be done. They took the initiative to apply for it and can recruit them.
Shutd0wn: Um
lengmo: [Security Research (Software Direction)_Chengdu] Tang Wenhan 1 year.docx
Shutd0wn: Well enough. Ji Yunhui is married
lengmo: 😂
2020-09-24 05:50:122020-12-01 03:27:49
lengmo: 404 wants to help us get through the water again
Shutd0wn: Which customer, how much amount. I heard that all 404 projects at the security port have been cancelled.
lengmo: 706. JG unit bar. 450W. Still ok, increase performance. Receive 5 points
Shutd0wn:Um
2020-12-01 03:29:55i-SOON as an APT:
The most brazen part about this leak is the open acknowledgement of i-SOON as a APT hacking unit for hire. In their product documentation it openly talks about their APT hacking services and that their main targets are India and Nepal Defense.

2021-04-19 02:28:13
Shutd0wn: What kind of people do you need? Please send us a specific request.
lengmo: Just penetrate the external network and internal network. 2 people. They mainly do APT, and this time they said they wanted to do Y.
Shutd0wn:Is it a choice between external network and internal network?
lengmo: Mainly the intranet is more focused. The main purpose of the external network is to enter the entrance, and it is definitely needed. They also want Yan Zhuang to go there... I say this is not necessarily the case, it needs to be coordinated.
2021-04-19 02:30:49 i-SOON Hacking Capabilites
Hacking Software Platforms
Great Firewall Bypass Router
OSINT data platform for Intelligence collection
Chinese Government work
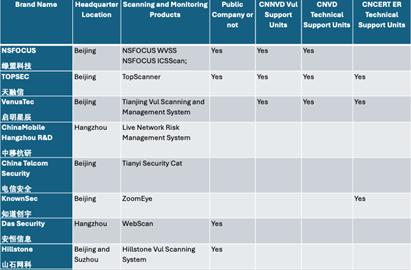
We could verify that i-SOON has many government connections and contracts as a supplier of cyber security software and services. They spoke about government contract work daily in their chatlogs and had a presence in many provinces supplying staff, training and products to government and industry. A few examples of this are:
- The Company has a financial relationship with the Chinese Government, with at least 1 verified winning bid for ¥580000.00 with what appears to be Sinochem but the tool and end client is not named. The announcement source was Military Weapons Tendering and Procurement Information Network which we must flag as the original source for this tender information. (Spooky).
- They had a secret military qualification clearance to receive defense work as evidence in their chat logs.
020-12-21 04:31:19
Shutd0wn Hey, Cao Jun and his company signed tens of millions this year
Obtained the military secret qualification in the same month as us
Y is giving me a blowjob
lengmo show off
It shows that JG is still okay
The industry can do it, but we people can’t
2020-12-21 04:33:39- Mei Danowski writing on her substack NATTO Thoughts also found that i-SOON were a qualified supplier for the Ministry of State Security.

- Sichuan Anxun Information Technology Co., Ltd received a thankyou letter we found from the Office of the Cybersecurity and Information Committee of the Chengdu Municipal Committee of the Communist Party of China, dated 18 Aug 2023.


Who is behind the leak?
I assess that the most likely candidate for this leak based on available evidence is APT41. The leaker has had complete access to internal company information including a compilation of chatlogs between staff using their WeChat IDs, sensitive product information and HR data. We can only guess that the leaker either themselves hacked i-SOON or the documents were provided to the leaker in full. We must note that we found evidence of a formal legal dispute between APT41 and i-SOON which brings up a possibility that this information was held as evidence in some type of discovery proceeding. APT41 themselves are a prime suspect to be the leaker in our view due to the legal motives they possess, their capability to hack others and that specific information about them had already been erased.